Data Centric Security Model
An approach that combines information security technologies with strategic business goals to determine the business value of data and to thereby enable a company to choose the most appropriate level of IT security.
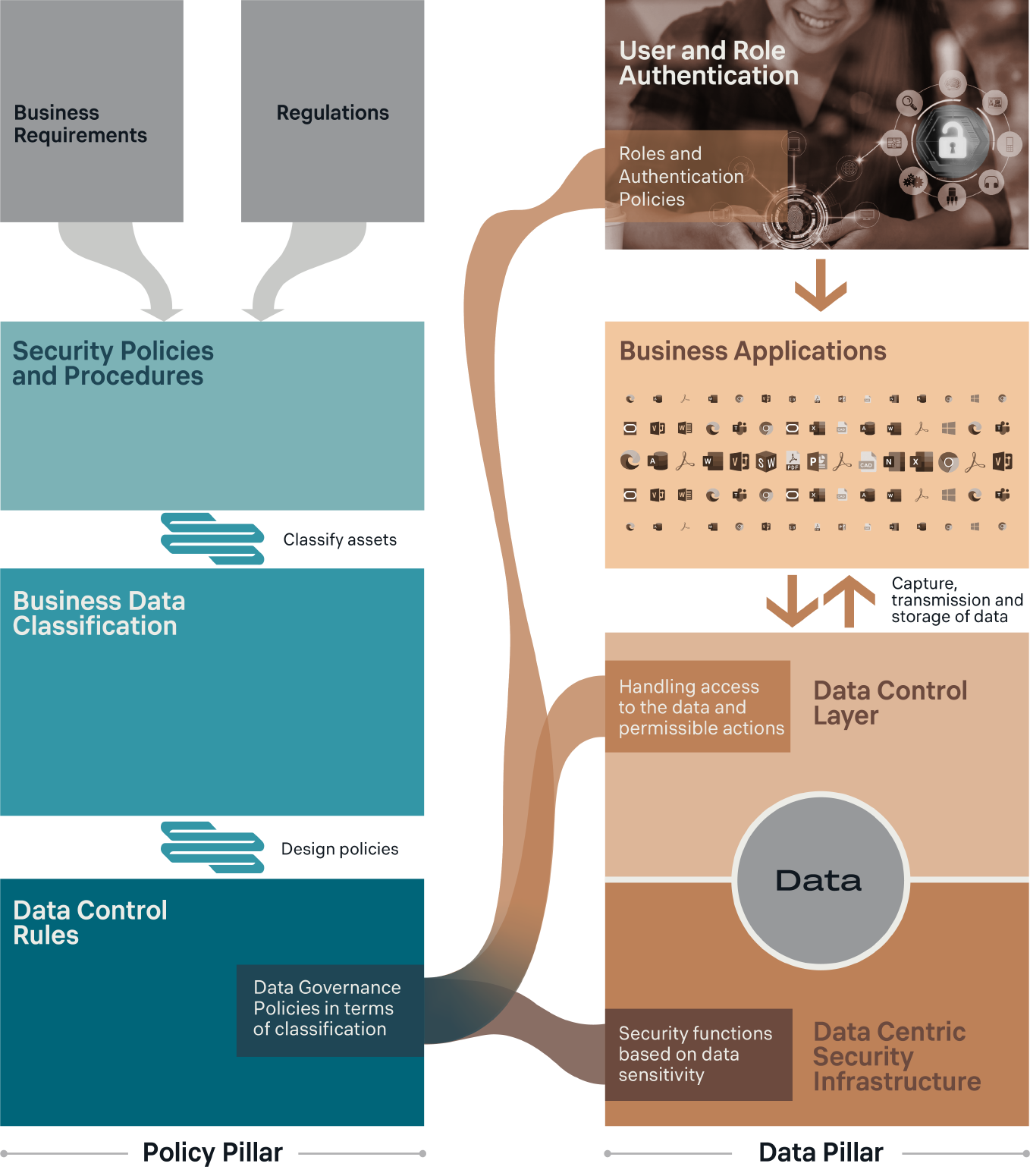
The Perimetrix approach is based on the DCSM (Data Centric Security Model), also known as the information centric security model. It was first defined¹ in 2007 and proposes the idea that data should classified based on its importance to the relevant business processes. In practical terms, this means that the level of security assigned to data must be appropriate given its business value.
This approach makes it possible to establish a link between the technical competence of information security specialists and the knowledge of data owners regarding the role of information in achieving business objectives.
The implementation of the DCSM approach begins with the creation of a set of corporate data processing guidelines. Then, security policies are defined and used to determine which information security services are necessary to support the established guidelines.
Following the identification of an organization’s information assets and the classification of business data, it is then possible to define business-oriented rules for data management. Rules are defined for each category of information, describing how the data should be used and by what means it should be protected.
These business-oriented data management rules are subsequently translated into security configuration settings for applications and services on user systems. This establishes a very strong connection between business and IT components which can be focused and applied to the required context.
By taking the core concept of the DCSM and implementing it in practice, Perimetrix solutions aim to ensure compliance with established policies for working with data as well as limiting deviations from said policies. Perimetrix’s approach to preserving the value of data is based on the fact that data used in business processes has its own specific life-cycle.
This essentially entails a list of operations performed with the data beginning from its creation all the way through to its retirement. During its life-cycle, the value of data as well as its level of confidentiality can increase, requiring adjustments related to its protection. In other words, adapting security in order to ensure the appropriate use of the data.
- 1 “Elevating the Discussion on Security Management — The Data Centric Paradigm” by IBM Research, IBM Security & Privacy Services, Zurich Financial Services; “Enterprise Security: A data — centric approach to securing the enterprise” by Aaron Woody.